
Cybersecurity
Protecting sensitive data, IT infrastructure and users
Get the confidence and high level of security for your valuable data and IT infrastructure with us. We provide key cybersecurity services such as vulnerability and policy compliance management, penetration testing, cybersecurity consulting, and the Axians Security Operations Center. We also offer network security and endpoint protection services.

Get the benefits with Axians:
CERTAINTY, EXPERTISE AND PROVEN SOLUTIONS
- reducing the security risk to the organisation
- a proven process for detecting and managing security incidents
- reduced response time to security events and incidents
- cost-effective resolution of security risks through prioritization
- compliance with security standards, laws and company policies, as well as IT best practices (CIS Benchmark)
- availability of cyber security experts without high recruitment and training costs
Vulnerability management in accordance with security policies
Do you know the weaknesses of your IT systems? With a cloud-based security platform, you get instant visibility into potential security threats and how to effectively defend against them. We prioritize identified vulnerabilities according to your company’s needs and risk profile. We design a complete vulnerability management architecture, provide implementation, scanning, reporting, automation and integration, and all follow-up steps to secure your IT infrastructure.

Penetration testing
Penetration testing uncovers vulnerabilities in your IT infrastructure and applications, revealing vulnerabilities and helping to prevent cyber attacks in the real world. We follow the most appropriate standards such as OSSTMM, PTES and OWASP for testing. The goal is to identify weaknesses and properly assess security risks for your company. You will receive a comprehensive report that includes a management summary as well as a detailed analysis of the individual findings, and in particular the corrective actions for each security threat.
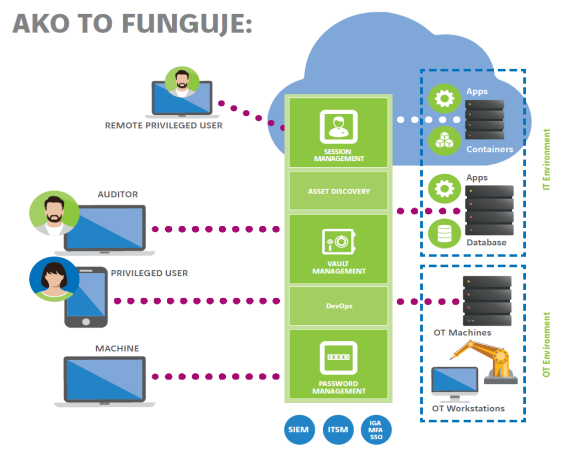
Managing administrator accounts
The Privileged Access Management (PAM) solution allows organizations to monitor and manage all actions performed by privileged users – administrators. PAM, combined with multi-factor authentication, authenticates and authorizes each administrator with such access. The solution streamlines the management and oversight of users with elevated access rights within an organization from accidental or intentional misuse. It is the misuse of a privileged account by one of the system administrators that represents the most commonly exploited vulnerability.

Advisory
FOR YOUR SECURITY STRATEGY
The right strategy and clear direction are essential to your company’s cybersecurity. Assessing the current state, defining the desired state and finding the path that leads to it is essential. Our certified experts can help you effectively achieve your cybersecurity goals, whether it’s enhancing security, developing procedures to address security incidents, or meeting specific standards or regulations in accordance with ISO 27 000 and ISA/IEC 62 443 for industrial systems.
Axians Security Operations Center (SOC)
Axians SOC protects your critical data and resources by monitoring your IT infrastructure in real time. The SIEM solution allows you to collect, analyze, correlate and evaluate logs from all the IT devices and security systems you use in your company. This allows us to quickly and accurately detect an incident, assess the priority and severity of the security threat, and then take action.
Other security services

Get in touch
"*" indicates required fields

